Add Fargate Profile
Create IAM OIDC provider
First, we will have to set up an OIDC provider with the cluster. The IAM OIDC Provider is not enabled by default, you can use the following command to enable it.
eksctl utils associate-iam-oidc-provider \
--region ${AWS_REGION} \
--cluster eksworkshop-eksctl \
--approve
Create the Namespace and IAM Role and ServiceAccount
We will create the prodcatalog-ns and the IRSA for this namespace which will give permission to X-Ray, AppMesh and Cloudwatch Logs policies.
kubectl create namespace prodcatalog-ns
cd eks-app-mesh-polyglot-demo
aws iam create-policy \
--policy-name ProdEnvoyNamespaceIAMPolicy \
--policy-document file://deployment/envoy-iam-policy.json
eksctl create iamserviceaccount --cluster eksworkshop-eksctl \
--namespace prodcatalog-ns \
--name prodcatalog-envoy-proxies \
--attach-policy-arn arn:aws:iam::$ACCOUNT_ID:policy/ProdEnvoyNamespaceIAMPolicy \
--override-existing-serviceaccounts \
--approve
The IAM role gets associated with a Kubernetes Service Account. You can see details of the service account created with the following command.
kubectl describe sa prodcatalog-envoy-proxies -n prodcatalog-ns
Learn more about IAM Roles for Service Accounts in the Amazon EKS documentation.
Create a Fargate profile
The Fargate profile allows an administrator to declare which pods run on Fargate. Each profile can have up to five selectors that contain a namespace and optional labels. You must define a namespace for every selector. The label field consists of multiple optional key-value pairs. Pods that match a selector (by matching a namespace for the selector and all of the labels specified in the selector) are scheduled on Fargate.
It is generally a good practice to deploy user application workloads into namespaces other than kube-system or default so that you have more
fine-grained capabilities to manage the interaction between your pods deployed on to EKS. In this chapter we will create a new Fargate profile named fargate-productcatalog
that targets all pods destined for the prodcatalog-ns namespace with label app: prodcatalog. You can see the Fargate Profile configuration below from clusterconfig.yaml.
Run the below command to create the Fargate Profile
cd eks-app-mesh-polyglot-demo
envsubst < ./deployment/clusterconfig.yaml | eksctl create fargateprofile -f -
When your EKS cluster schedules pods on Fargate, the pods will need to make calls to AWS APIs on your behalf to do things like pull container images from Amazon ECR. The Fargate Pod Execution Role provides the IAM permissions to do this. This IAM role is automatically created for you by the above command.
Creation of a Fargate profile can take up to several minutes. Execute the following command after the profile creation is completed and you should see output similar to what is shown below.
The creation of the Fargate Profile will take about 5 - 7 minutes.
eksctl get fargateprofile --cluster eksworkshop-eksctl -o yaml
Log into console and navigate to Amazon EKS -> Cluster -> Click eksworkshop-eksctl -> Configuration -> Compute, you should see the new Fargate Profile fargate-productcatalog you created:
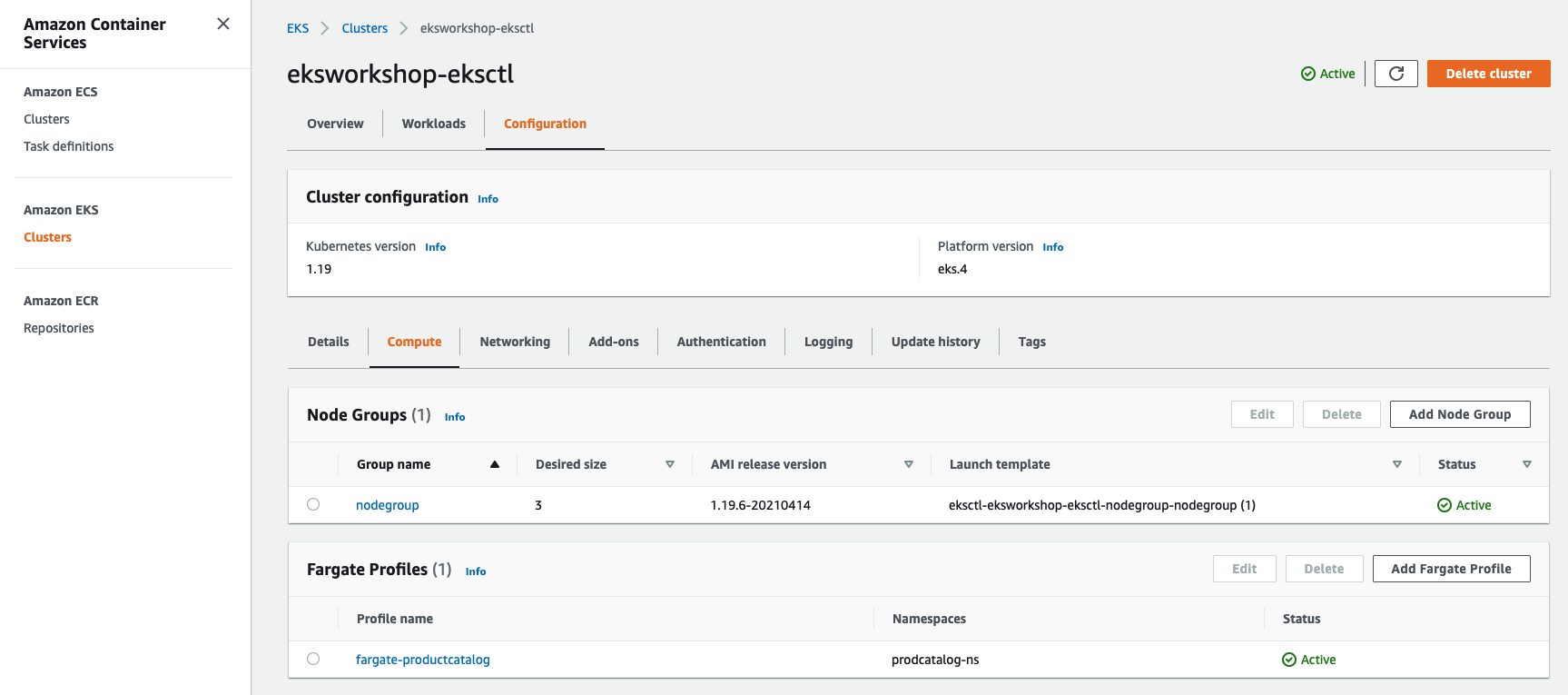
Notice that the profile includes the private subnets in your EKS cluster. Pods running on Fargate are not assigned public IP addresses, so only private subnets (with no direct route to an Internet Gateway) are supported when you create a Fargate profile. Hence, while provisioning an EKS cluster, you must make sure that the VPC that you create contains one or more private subnets. When you create an EKS cluster with eksctl utility, under the hoods it creates a VPC that meets these requirements.