Security groups for pods
Introduction
Containerized applications frequently require access to other services running within the cluster as well as external AWS services, such as Amazon Relational Database Service (Amazon RDS).
On AWS, controlling network level access between services is often accomplished via security groups.
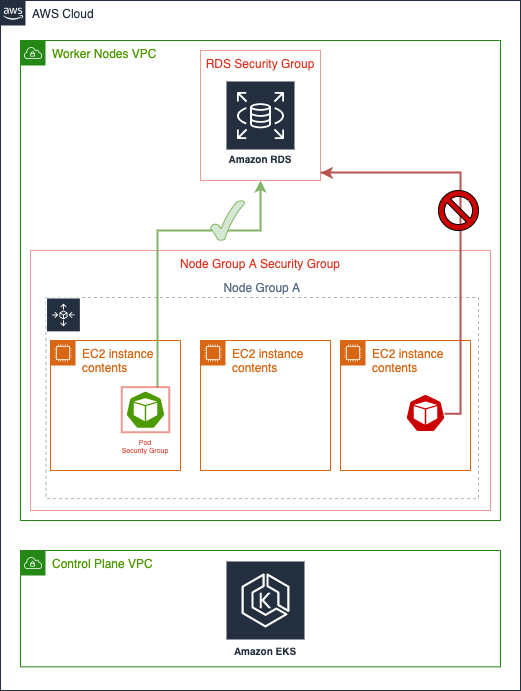
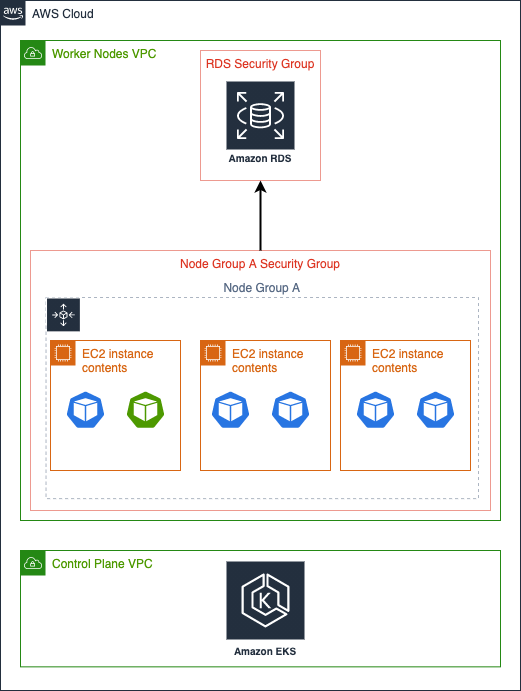
Before the release of this new functionality, you could only assign security groups at the node level. And because all nodes inside a Node group share the security group, by attaching the security group to access the RDS instance to the Node group, all the pods running on theses nodes would have access the database even if only the green pod should have access.
Security groups for pods integrate Amazon EC2 security groups with Kubernetes pods. You can use Amazon EC2 security groups to define rules that allow inbound and outbound network traffic to and from pods that you deploy to nodes running on many Amazon EC2 instance types. For a detailed explanation of this capability, see the Introducing security groups for pods blog post and the official documentation.
Objectives
During this section of the workshop:
- We will create an Amazon RDS database protected by a security group called RDS_SG.
- We will create a security group called POD_SG that will be allowed to connect to the RDS instance.
- Then we will deploy a
SecurityGroupPolicythat will automatically attach the POD_SG security group to a pod with the correct metadata. - Finally we will deploy two pods (green and red) using the same image and verify that only one of them (green) can connect to the Amazon RDS database.