Testing the Application
Now it’s time to test.
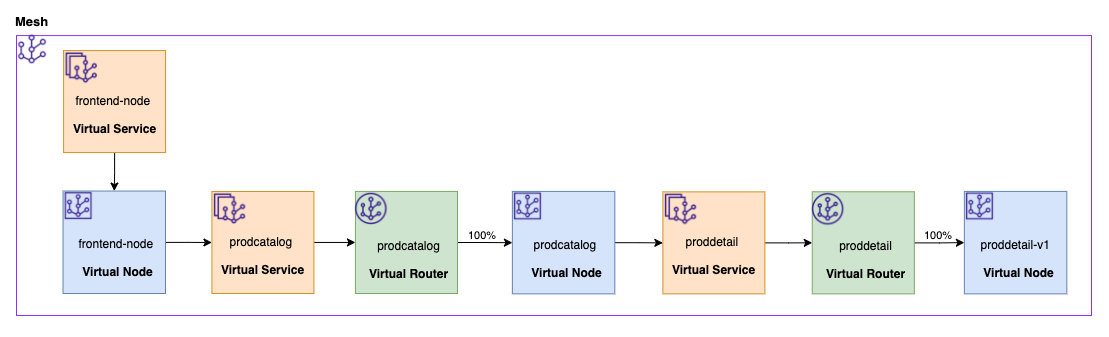
To test if our ported Product Catalog App is working as expected, we’ll first exec into the frontend-node container.
export FE_POD_NAME=$(kubectl get pods -n prodcatalog-ns -l app=frontend-node -o jsonpath='{.items[].metadata.name}')
kubectl -n prodcatalog-ns exec -it ${FE_POD_NAME} -c frontend-node bash
You will see a prompt from within the frontend-node container.
Test the confiuration by issuing a curl request to the virtual service prodcatalog on port 5000, simulating what would happen if code running in the same pod made a request to the prodcatalog backend:
curl -v http://prodcatalog.prodcatalog-ns.svc.cluster.local:5000/products/
Output should be similar to below. You can see that the request to backend service prodcatalog is going via envoy proxy.
Exit from the frontend-node exec bash.
Now, To test the connectivity from Fargate service prodcatalog to Nodegroup service proddetail, we’ll first exec into the prodcatalog container.
export BE_POD_NAME=$(kubectl get pods -n prodcatalog-ns -l app=prodcatalog -o jsonpath='{.items[].metadata.name}')
kubectl -n prodcatalog-ns exec -it ${BE_POD_NAME} -c prodcatalog bash
You will see a prompt from within the prodcatalog container.
Test the confiuration by issuing a curl request to the virtual service proddetail on port 3000, simulating what would happen if code running in the same pod made a request to the proddetail backend:
curl -v http://proddetail.prodcatalog-ns.svc.cluster.local:3000/catalogDetail
You should see the below response. You can see that the request to backend service proddetail-v1 is going via envoy proxy. You can exit now from the prodcatalog exec bash.
Congrats! You’ve migrated the initial architecture to provide the same functionality. Now lets expose the frontend-node to external users to access the UI using App Mesh Virtual Gateway.