Pods Deployments
Kubernetes secrets
Before deploying our two pods we need to provide them with the RDS endpoint and password. We will create a kubernetes secret.
export RDS_PASSWORD=$(cat ~/environment/sg-per-pod/rds_password)
export RDS_ENDPOINT=$(aws rds describe-db-instances \
--db-instance-identifier rds-eksworkshop \
--query 'DBInstances[0].Endpoint.Address' \
--output text)
kubectl create secret generic rds\
--namespace=sg-per-pod \
--from-literal="password=${RDS_PASSWORD}" \
--from-literal="host=${RDS_ENDPOINT}"
kubectl -n sg-per-pod describe secret rds
Output
Deployments
Let’s download both pods deployment files
cd ~/environment/sg-per-pod
curl -s -O https://www.eksworkshop.com/beginner/115_sg-per-pod/deployments.files/green-pod.yaml
curl -s -O https://www.eksworkshop.com/beginner/115_sg-per-pod/deployments.files/red-pod.yaml
Take some time to explore both YAML files and see the different between the two.
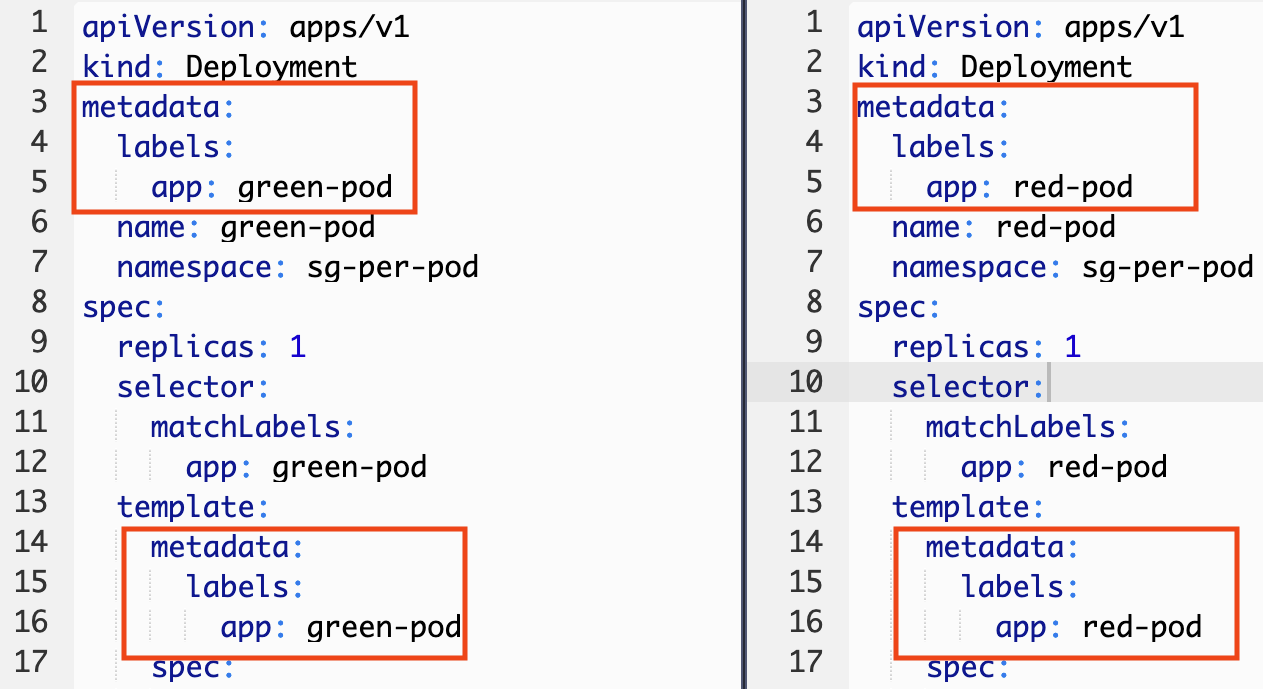
Green Pod
Now let’s deploy the green pod
kubectl -n sg-per-pod apply -f ~/environment/sg-per-pod/green-pod.yaml
kubectl -n sg-per-pod rollout status deployment green-pod
The container will try to:
- Connect to the database and will output the content of a table to STDOUT.
- If the database connection failed, the error message will also be outputted to STDOUT.
Let’s verify the logs.
export GREEN_POD_NAME=$(kubectl -n sg-per-pod get pods -l app=green-pod -o jsonpath='{.items[].metadata.name}')
kubectl -n sg-per-pod logs -f ${GREEN_POD_NAME}
Output
use CTRL+C to exit the log
As we can see, our attempt was successful!
Now let’s verify that:
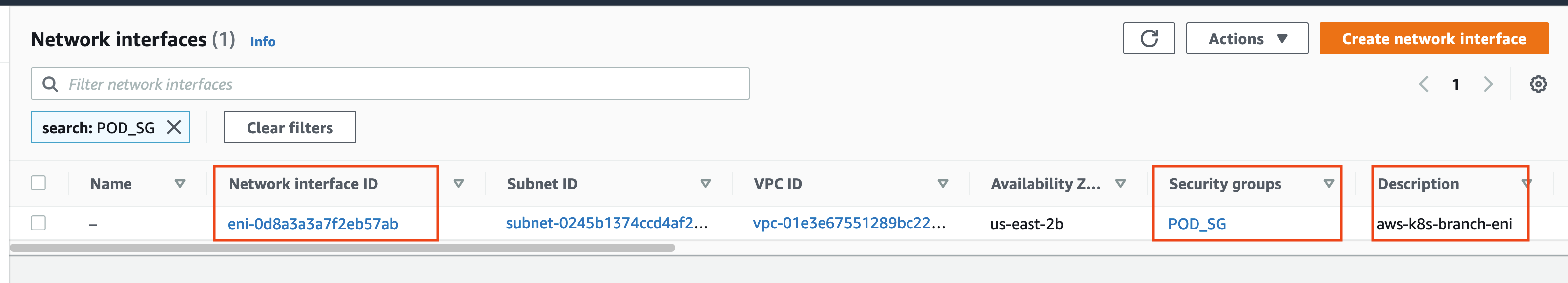
- An ENI is attached to the pod.
- And the ENI has the security group POD_SG attached to it.
We can find the ENI ID in the pod Annotations section using this command.
kubectl -n sg-per-pod describe pod $GREEN_POD_NAME | head -11
Output
You can verify that the security group POD_SG is attached to the eni shown above by opening this link.
Red Pod
We will deploy the red pod and verify that it’s unable to connect to the database.
Just like for the green pod, the container will try to:
- Connect to the database and will output to STDOUT the content of a table.
- If the database connection failed, the error message will also be outputted to STDOUT.
kubectl -n sg-per-pod apply -f ~/environment/sg-per-pod/red-pod.yaml
kubectl -n sg-per-pod rollout status deployment red-pod
Let’s verify the logs (use CTRL+C to exit the log)
export RED_POD_NAME=$(kubectl -n sg-per-pod get pods -l app=red-pod -o jsonpath='{.items[].metadata.name}')
kubectl -n sg-per-pod logs -f ${RED_POD_NAME}
Output
Finally let’s verify that the pod doesn’t have an eniId annotation.
kubectl -n sg-per-pod describe pod ${RED_POD_NAME} | head -11
Output
Conclusion
In this module, we configured our EKS cluster to enable the security groups per pod feature.
We created a SecurityGroup Policy and deployed 2 pods (using the same docker image) and a RDS Database protected by a Security Group.
Based on this policy, only one of the two pods was able to connect to the database.
Finally using the CLI and the AWS console, we were able to locate the pod’s ENI and verify that the Security Group was attached to it.